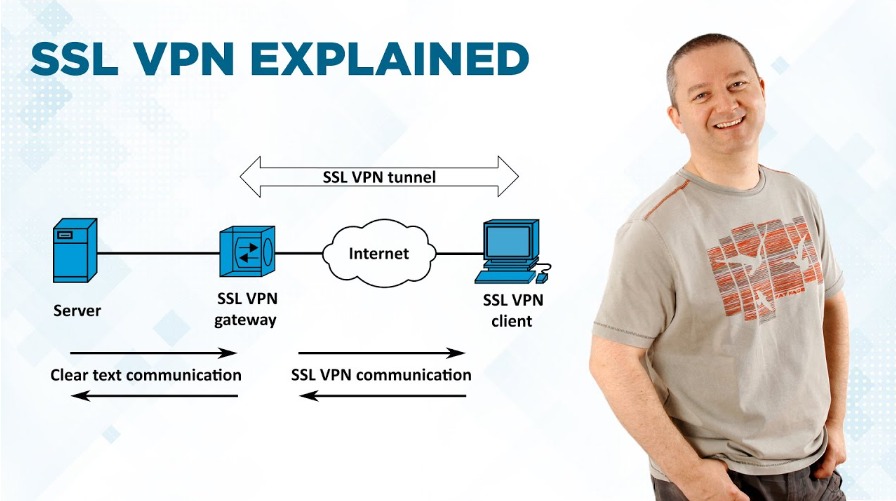
SSL VPNs are great for businesses looking to quickly and easily provide remote access to network applications. Unlike IPSec VPNs, they don’t require a specific client app or software on users’ devices – all you need is a modern web browser. Ensure your employees, contractors, and partners have full, secure access to work applications anywhere. SSL VPNs are the solution.
Privacy
As a network security solution, an SSL tunnel VPN uses a standard encryption protocol that secures all client and server communication. This protects data from unauthorized access as it travels over the internet, keeping sensitive information and applications private from prying eyes. Users connect to the SSL VPN gateway over any modern web browser. Once a connection is established, users can access multiple networks and applications from their devices. This includes cloud-based Software-as-a-Service (SaaS) apps and any other private network services defined by an organization’s IT team. The benefit of this is that it allows remote employees to work from anywhere, on any device, without compromising the company’s security standards and policies. It also reduces IT overhead and support costs, as the solution doesn’t require any specific driver or software installations since it works with any widely used web client.
Security
One of the primary advantages of SSL Tunnel VPN over other VPN protocols like IPsec is that it relies on standardized TLS technologies implemented in most web browsers, so network administrators don’t need to install additional software on remote devices. This helps reduce support overhead and complexity and makes it easier to deploy. Another security advantage is that it encrypts data sent between the server and end-user device, so hackers can’t intercept remote users’ communications to steal sensitive information such as login credentials or financial information. The tunneling nature of the SSL protocol also prevents hackers from executing “man-in-the-middle” attacks to gain access to company networks and cause significant damage. The gateway server of an SSL Tunnel VPN also integrates with the company’s authentication systems to provide granular access control. This allows network administrators to set restrictions with surgical precision so hacking opportunities are minimized. This makes the SSL Tunnel VPN an excellent option for secure remote access for employees in various scenarios. A notable drawback of the SSL Portal VPN is that it can only tunnel to web-enabled SSL applications and doesn’t allow access to physical network resources such as printers.
Convenience
The best part about SSL VPN is that it’s easy to set up and maintain. Unlike other types of VPNs requiring specific drivers and software, SSL VPN is based on the TLS protocol and works across most browsers on desktop computers and mobile devices. This allows remote workers to start instantly, and administrators don’t have to worry about complicated software installations or deployments. Once the connection is established, SSL VPN encrypts all client and server transactions. This helps prevent eavesdropping and snooping from unwanted sources. However, it’s important to note that only data explicitly transmitted through the VPN tunnel will be protected. Other apps and programs on a computer can still be susceptible to malware and phishing attacks. SSL VPNs differ from others because they can only connect to web-enabled applications and network services. This limits what a remote worker can do, but in some cases, this is a good thing. Using an SSL portal can help limit the number of available applications and encrypt all traffic between them, making it much more difficult for attackers to access internal company resources.
Flexibility
SSL Tunnel VPN is an alternative to IPSec VPN solutions. While IPSec requires client software on remote users’ systems, SSL Tunnel VPNs connect through Web browsers using existing technologies. This allows for quicker deployment and reduces administrative costs for enterprises. It also provides flexibility in network access, as SSL Tunnel VPNs can support protocols and applications that aren’t web-based. However, it does require a browser that can handle active content. This means that users with outdated browsers cannot use the VPN. Another advantage of SSL Tunnel VPN is that it can limit tunneling to specific apps instead of the entire network, making it easier for administrators to enforce more precise security policies. Granular tunneling makes it easier to balance functionality and privacy, which can be especially important for organizations that need to secure sensitive data on a mobile device. This includes financial transactions, medical communications, and proprietary corporate networks. Secure communication is necessary for these applications, and securing this data in-app helps protect it from malware threats.
Scalability
As the number of work-from-home and remote workers grows, organizations must provide secure access to multiple devices. An SSL Tunnel VPN uses TLS protocol technology, already implemented in most web browsers. This eliminates the need to install client software on each device and simplifies maintenance, as updates are pushed to users by their browser rather than requiring internal IT support. In addition, an SSL Tunnel VPN can provide a more versatile connection to networks and applications than an essential SSL Portal VPN. An SSL Tunnel VPN requires a browser that can handle active content, allowing for additional functionality beyond a simple SSL Portal. Granular policies also allow the SSL VPN to funnel traffic to specific applications, even when networkwide access is unnecessary. This can help optimize performance, reduce security risks, and ensure access rights are revoked when employees’ roles change. Before deploying this solution, it is essential to perform thorough testing and verification to confirm that routing rules function as intended for all applications, use cases, and device types.